And then there was 5… Only 5 sections left in Cisco CCNA 200-301 – The Complete Guide to Getting Certified. I have really enjoyed Neil Anderson’s course and I am feeling very confident about the test coming up at the end of the month.
Check the course out on Udemy: https://www.udemy.com/course/ccna-complete/
Neil Anderson’s Youtube Channel Flackbox: https://www.youtube.com/channel/UCVOdgH0-GrxtAFSZjHVEB0A
Website flackbox.com
Section 35: QoS – Quality of Service
- Overview
- The first need to QoS was VoIP
- Traditionally each service would have its own network
- The phone would use PBX and go over Public Switch Telephony Network
- Video chat would use an ISDN
- Computer over an IP WAN
- Modern networks will go over the same IP infrastructure
- This still requires a connection to the Public Switched Telephony Network
- Enable cost savings
- Increased features
- Data, voice, and video are all fighting for the same shared bandwidth
- Voice and standard video packets must meet these recommended requirements for acceptable quality
- Latency (delay) less or equal 150 ms
- Jitter (variation in delay) less or equal 30 ms
- VoIP systems attempt to smooth out the packets coming in to make the call sound natural so jitter needs to be low for the jitter buffer to work correctly
- Lossless or equal 1%
- HD video has higher requirements, any loss at all you will start to notice issues
- FIFO – First In First Out
- When congestion occurs on ta router or switch packets are sent out in a FIFO manner by default
- Congestion is when more traffic is coming in than what is being sent out.
- Effect of Congestion
- Delays of packets while they wait in the queue
- Queue size can affect jitter
- The packet can be drop if the queue is full
- Lower quality to an unacceptable level for voice and video
- Dealing with Congestion
- Add more bandwidth (cost more money
- Use QoS to deliver better service to specified traffic
- QoS will deliver packets quicker and overwrite the FIFO default behavior based on QoS classification
- Effects of QoS queuing
- Reduce delivery time (latency, jitter, and loss for specified traffic
- Can be used for more than Voice and Video, but for any specified traffic
- Other traffic that is not part of the QoS may receive worse services due to QoS traffic being delivered first
- QoS is used to mitigate temporary periods of congestion, and more bandwidth is recommended on lines that have consistent congestion
- Classification and Marking
- Identifying Traffic
- COS (Class of Service) marking
- 3 bits field in the Layer 2 802.1q frame header
- Value of 0-7 can be set, default is zero (designates as Best Effort)
- Higher the number, the higher the priority
- Value 6-7 are reserved for network use
- IP phones mark their call signaling traffic as CoS 3 and voice payload CoS 5
- DSCP (Differentiated Service Code Point) marking
- The preferred classification as it can be identified easily was as ACL and NBAR take more processor cycles to identify
- Layer 3 ToS (Type of Service) byte
- 6 bits so 64 possible values, default is zero (designates as Best Effort)
- IP phones mark the call signaling traffic as 23 (CS3) and voice payload 46 (EF)
- Standard 26 (AF31) for mission-critical data and 24 (AF41) for SD video.
- Access Control List
- Phone and voice set their own DSCP and CoS but if other traffic needs to be set for QoS it is unlikely that the application with be able to mark its own traffic.
- Use ACL to designate traffic
- NBAR (Network-Based Application Recognition)
- Uses Layer 3-7 information to identify traffic
- Can download signatures from Cisco to be loaded on routers to recognize well know applications
- Trust Boundary
- Switch router should not trust the PC that might be behind the phone
- Trust sources
- Phone can set both the COS (Layer 2) and DSCP (Layer 3)
- Layer 4 uses UDP Port
- If NBAR or ACL is used it should be done as close to the source as possible (First switch if possible).
- The classification does not change the service itself and only identifies the traffic
- Congestion Management
- Can manage switch and router congestion using queuing
- Bandwidth guarantees to specified traffic using CBWFQ (Class-Based Weighted Fair Queuing)
- LLQ (Low Latency Queuing) is CBWFQ with a priority queue
- Traffic in the priority queue is sent before other traffic
- MQC – Modular QoS CLI
- Has 3 main sections
- Class Maps define the traffic to take action on
- Policy Maps take the action on that traffic
- Service Policies apply the policy to an interface
- MQC was first used for QoS but it is now used in other location like Firewall rules
- Command Example
- Configure the same LLQ policy on the routers in both locations (internal call)
- Apply to WAN interfaces
- Policy-map will not be applied unless there is congestion detected
- Create Class map
- class-map VOICE-PAYLOAD
- match ip dscp ef
- class-map CALL-SIGNALING
- match ip dscp cs3
- Apply Class Map to Policy-map
- policy-map WAN-EDGE
- class VOICE-PAYLOAD
- priority percent 33
- class CALL-SIGNALING
- bandwidth percent 5
- class class-default
- fair-queue
- class class-default is all other traffic
- fair-queue is a better queuing system than FIFO as FIFO tends to penalize smaller packet
- Apply Policy-map to interface
- int serial0/0/0
- bandwidth 768
- service-policy out WAN-EDGE
- For the test, you do not need to know the configuration but you need to know and understand the theory behind the mappings and “Policy and Shaping”
- Policing and Shaping
- Can be used to control the traffic rate
- Measure the rate of traffic through an interface and take action if above-configured limits
- Traffic shaping buffers excess traffic so overall traffic stays in the desired rate limit
- Policing drops or re-marks traffic to enforce rate limits
- Classification can be used in policing and shaping to allow different rates for different types of traffic
- Policing
- Example
- ISP
- Set policing policy to set bandwidth for customer
- Worm/Junk traffic
- Mark worms and junk traffic like p2p as ‘Scavenger’ traffic
- Recommended DSCP value to be marked DSCP 8 (CS1)
- Use to limit junk traffic down to prevent it from taking bandwidth from business applications
- Shaping Scenario
- As the ISP has a Policing policy that will drop packets if it goes over, the internal side can set a shaping policy to have all traffic be sent within the ISP limits
- After setting the policing policy a congestion policy needs to be put in place also
- As only one policy map can be set to an interface, other policy needs to be nested into the shaping policy
Section 36: Cloud Computing
- Test Notes
- Will not test on configuration
- Will test on the theory of cloud computing
- Service Modules
- Deploy Models
- Traditional Deployment Models
- On Prem
- All equipment located in the building
- Owned by you
- A clear line of who owns what
- Equipment is CapEx (Capital Expenditure)
- Can take over a week to receive and deploy
- Need a planned refresh of equipment
- Plan redundancy
- Colo
- Owned Equipment located in a rented space/data center
- The datacenter provides services like power, cooling, physical securing, networking, and internet connections
- Service provided through an SLA
- The connection from corp buildings and colo are the responsibility of ISPs
- Defining Cloud Computing
- NIST Definition: Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access toa shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction.
- NIST Characstics
- On-Demand Self-Serice: A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
- Rapid Elasticity: Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time.
- Broad Network Access: Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms.
- Resource Pooling: The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand.
- Measured Service: Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service.
- Cloud Service Models
- Models define where the customer and providers areas of responsibility are and what level the customer gains access
- The models build on top of one another
- Models
- IaaS – Infrastructure as a Service
- Provides: Facility->Network->Storage->Computer->Hpervisor
- Paas – Platform as a Service
- Provides: Facility->Network->Storage->Computer->Hpervisor->Operating System
- SaaS – Software as a Service
- Provides: Facility->Network->Storage->Computer->Hpervisor->Operating System-Application->Data
- Cloud Deployment Models
- Public Cloud
- The cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or government organization, or some combination of them. It exists on the premises of the cloud provider.
- Well known providers
- AWS
- Azure
- IBM Bluemix
- Salesforce
- Most common deployment
- Private Cloud
- The could infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers. It may be owned, managed, and operated by the organization, a third party, or some combination of them and it may exist on or off-premises.
- Private Cloud works the same way as Public Cloud, but the services are provided to internal business units instead of to external public enterprises.
- Fulfills the cloud ‘Essential Characteristics’
- On-Demand Self-Service
- Rapid Elasticity
- Broad Network Access
- Resource Pooling
- Measured Service
- The company will use automation software such as Cisco UCS Director
- DNA Center can be used as an SDN controller
- Community Cloud
- The cloud infrastructure is provisioned for exclusive use by a specific community of consumers from organizations that have shared concerns.
- This is the least common deployment model. It is sometimes used in government environments.
- Hybrid Cloud
- the cloud infrastructure is a composition of two or more distinct could infrastructures that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability.
- Cloud Computing Advantages
- Scalability
- Ability to regulate the service in accordance with their current requirements:
- Scale capacity up and down
- Infinite computing capacity on demand
- Flexibility through cloud bursting
- Agility
- Ability to handle expected or unexpected changes in load
- Reduced time to deploy
- Cost Efficiency
- pay for what you need
- Avoid provisioning and pay for the peak as a permanent fixture
- Move from a large upfront CapEx cost to a comparatively small monthly OpEx cost
- ICT costs are more transparent
- Do not have depreciable hardware assets
- The provider is responsible for tech refresh
- Predictable monthly fee.
- Competitive Advantage
- Traditional CapEx can be directed to other investments
- Can respond quickly to evolving markets and on growing business core
- Productivity
- IT staff can focus on strategic decisions and developing and improving core applications rather than maintaining or troubleshooting hardware infrastructure.
- Does not mean that in-house IT is not needed. Deploying in the public cloud is just like deploying in-house. IT is able to focus on design, security, and support of the applications and data opposed to hardware.
- Availability and Reliability
- Facilities are located in hardened data centers
- redundant power
- onsite security
- no single point of failure
- Certified with standards such as ISO 9001 and 27001
- Data centers follow best practices for facilities, server, networking and storage
- Provide SLA
- Cost
- Advantages usually come down to Cloud Computing usually comes down to the overall long-term cost
- Compare TCO of On-Premises Vs Cloud Equivalent.
- Most companies use a mix of On-Premises and Cloud solutions
Section 37: Wireless Network Fundamentals
- Wireless Network Types
- 802.11 WiFi Standard
- WPAN – Wireless Person Area Network
- Devices are within 10 meters of each other
- Bluetooth is often used
- WLAN: Wireless Local Area Network
- CCNA focuses on WLAN
- Provides access to a campus network, without the need for a cable
- Devices within 100m of a WAP (Wireless Access Point
- WMAN: Wireless Metropolitan Area Network
- Covers a large area such as a city
- Modes
- Ad Hoc Networks
- Two or more wireless stations communicate directly with each other
- IBSS – Independent Basic Service Set
- Infrastructure Mode
- Stations communicate via a Wireless Access Point (AP)
- This can provide access to a wired network
- Multiple APs can be deployed for coverage
- WiFi Direct
- Allows the device to be connected to an AP and also be part of a peer-to-peer wireless network
- Does not operate in Ad-Hoc IBSS mode, it is an extension to Infrastructure Mode
- WPS WiFi Protected Setup enables connection setup by pushing a button
- GARBAGE… DO NOT USE NOT SECURE (This comment is not part of CCNA)
- It is WPAN
- Services
- Miracast
- DLNA – Digital Living Network Alliance – allows devices to stream music and video
- Direct Print
- Wireless Bridge
- Used to connect areas which are not reachable via cable
- Mesh Networks
- Spread the coverage area
- One AP radio is used to serve the client
- Other radios connect to the backhaul network
- Infrastructure Mode and Wireless Access Points (WAP)
- WAP provides connectivity between wireless stations and between the wireless and wired network
- Wireless is half-duplex
- One device can communicate at a time
- BSS – Basic Service Set
- Access Point centralizes access and control over a group of wireless devices
- the device and their wireless setting makeup a BSS
- DS – Distribution System
- A distribution system connects WAP to the wired network
- BSSID – Basic Service Set Identifier
- Devices within BSS are identified by the BSSID, which is based on their MAC address
- BSA – Basic Service Area
- The BSA is the wireless coverage area of an Access Point
- AKA wireless cell
- SSID – Service Set Identifier
- A unique identifier that names the wireless network
- Multiple SSID Service Set Identifiers
- A single AP can support multiple SSIDs
- Different SSIDs can have different security settings and be mapped to different VLANs
- Beacons
- WAP broadcast information about their WLANs with beacon frames
- This can be disabled
- ESS – Extended Service Set
- The same SSID across multiple AP to increase the coverage area
- Roaming
- Clients can roam across APs supporting the same WLAN
- WLC – Wireless LAN Controllers and CAPWAP
- Configuring a large amount of APs one by one becomes unmanageable
- WLC is a centralized device to manage all APs
- Virtual WLC is available
- Redundancy is support
- Autonomous vs Lightweight Access Point
- Autonomous APs are standalone APs
- Lightweight AP are WLC controlled
- Installed software image determines whether an AP is autonomous or Lightweight
- ZTP – Zero Touch Provisioning
- Lightweight AP support Zero Touch Provisioning
- They discover their wireless LAN Controller via these options:
- DHCP – option 43 gives the IP address of the WLC
- DNS – ‘cisco-capwap-controller’ resolves the IP address of the WLC
- Local subnet broadcast
- Wireless Access Points
- AP downloads it configuration from the WLC
- Includes what WLANs it should support and their settings
- The WLC also monitors the wireless quality and controls the channels and power of the Access Points
- Can detect rogue APs
- Roaming with WLC
- Stations can roam between APs cells that have the same WLANs
- Infrastructure can be configured to be seamless
- CAPWAP – Control and Provisioning of Wireless Access Points
- Communications are encrypted in a DTLS CAPWAP tunnel
- Uses UDP port 5246 and 5247
- management traffic between the AP and WLC passes through the CAPWAP tunnel
- LAG (Link Aggregation is often used on the WLC to switch link
- Split MAC
- Work is moved from the AP to the WLC
- Real-time traffic is handled by the AP to provide suitable performance, the rest is handled by the WLC
- Work is split between the AP and WLC hence the name ‘Split MAC’
- AP Operations
- Client handshake when connecting
- Beacons
- Performance monitoring
- Encryption and decryption
- Clients in power save
- WLC operations
- Auth
- Roaming control
- 802.11 to 802.3 communication
- Radio Frequency mgmt
- Security mgmt
- QoS mgmt
- FlexConnect
- Traffic is forwarded locally when FlexConnect is configured, keeping it from being sent to a WLC in another location. Example AP in Los Angeles and WLC NYC
- This useful for small branch offices without a Wireless LAN Controller
- Switch Configuration for Wireless Networks
- Autonomous AP
- Switch Commnads
- Create VLANs that each SSID will exist on
- (config)#vlan 21
- config-vlan)#name [VLAN1 Name]
- (config)#vlan 22
- (config-vlan)#name [VLAN2 Name]
- Configure the Switch the AP is plugged into
- (config)#interface gig1/0/1
- (config-if)#switchport trunk encap dot1q
- (config-if)#switchport mode trunk
- (config-if)#switchport trunk allowed vlan 21,22
- CAPWAP
- AP sends traffic to the WLC over the CAPWAP tunnel and does not tag the traffic for the specified VLAN
- The WLC will tag traffic and send it to the correct VLAN and send it to the switch for final delivery
- Link between the WLC and switch needs to be a trunk but the link between the AP and the switch should remain an access port on the management vlan that the CAPWAP uses.
- Commands
- Create VLANs that each SSID will exist on
- (config)#vlan 21
- config-vlan)#name [VLAN1 Name]
- (config)#vlan 22
- (config-vlan)#name [VLAN2 Name]
- Create WLC management and AP management VLANs
- (config)#vlan 10
- (config-vlan)#name [WLC MGMT name]
- (config)#vlan 11
- (config-vlan)#name [AP MGMT name]
- Configure Switch ports for WLC
- (config)#int gig1/0/2
- (config-if)#switchport trunk encap dot1q
- (config-if)#switchport mode tunk
- (config-if)#switchport trunk allowed vlan 10,11,21,22
- Configure Switch port for AP
- (config)#int gig1/0/1
- (config-if)#switchport mode access
- (config-if)#switchport access vlan 11
- Wireless Channels and RF (Radio Frequencies)
- Operate in the 2.4 and 5 GHz frequency spectrum
- Allocated for ISM (industrial, scientific and medical) use
- No radio operator’s license is needed
- No regulatory protection against interference from other users of the band.
- IEEE 802.11 Standards
- Standard – Year – Frequency – Data rate – Backward Compatibility
- 802.11 – 1997 – 2.4 GHz – 1, 2
- 802.11a – 1999 – 5 GHz – 6, 9, 12, 18, 24,36, 48, 54
- 802.11b – 1999 – 2.4 GHz – 1, 2, 5.5, 11
- 802.11g – 2003 – 2.4 GHz – 6, 9, 12, 18, 24, 36, 48, 54 – 802.11b 1, 2, 5.5, 11
- 802.11n – 2009 – 2.4 & 5 GHz – up to 600, Compatible with a, b, g
- 802.11ac – 2013 – 5 GHz – up to 3500, compatible with a and n
- Cisco AP support all standards
- 2.4 GHz Spectrum
- ranges from 2.4 to 2.4835
- Channels are 22 MHz ranges
- 14 Channels
- Standard non-overlapping channels 1, 6, 11
- Each AP operates in one channel
- Overlapping channels can cause interference with each other
- Access Points with overlapping server areas should use non-overlapping channels
- 5 GHz Spectrum
- Channels are 20 MHz
- Less overlapping
- Neighboring APs should be separated by at least one channel
- Channels can be bonded to multiply data rates by 2, 4 or 8x
- Interference
- 2.4 – there are many devices in this range
- Microwave
- Wireless Video Cameras
- Fluorescent Lights
- Baby Monitors
- 2.4 vs 5 GHZ
- 2.4 has greater range and is able to propagation through obstacles better
- 2.4 is more crowded
- 5 GHz 802.11ac has higher throughput than is available with 2.4 GHz
- Site Surveys
- Used to design layout of AP
- Maximum coverage of the required area
- Minumum leakage
- Discover potential sources of interference
- WLC can manage channel allocation and power levels of APs
- inSSIDer – Free software to see SSIDS in the area
- Wireless Security
- Leakage, this is when a signal goes outside of the wanted area
- No physical is needed to join the network
- More vulnerable to attack
- Strong auth and encryption should be used
- Security Standards
- WEP – Wired Equivalent Privacy (1999) – RC4 encryption
- WPA WiFi Protected Access (2003) – RC4 Encryption, TKIP (Temporal Key Integrity Protocol)
- WPA2 (2004) – AES encryption, CCMP Counter Cipher Mode with Block Chaining Message Authentication Code protocol
- WPA3 (2018) – AES encryption, CCMP, protection against KRACK attack
- WPA Personal/Enterprise
- Personal uses pre-shared keys (PSKs)
- Enterprise uses a AAA server
Section 38: Network Automation and Programmability
- Taditionalnetwork management
- Manage a single device at a time over SSH or GUI tools
- Copy and pasting from a text file
- NMS – Network Mangement Systems
- Use protocols such as SNMP and NetFlow to gather info/state of the network
- SNMP used to push configuration, can be complex
- SNMP has security concerns
- Issues
- Time consuming configuring one device at a time
- likelihood of typos/other mistakes
- Having many admins lead to difficult change control handling
- Easy to get non-standard configurations which are diffucult to troubleshoot
- Network Automation
- Use for
- Device configuration
- Initial device provisioning
- Software Version Control
- Collecting Statistics from devices
- Compliance verification
- Reports Troubleshooting
- Automation Benefits
- network programmability enables automation, reducing human to machine interaction
- Reducing human error such a typos
- Moden tools have been built with monitoring, configuration and troubleshooting in mind
- More scalable than configuring one device at a time
- Provide configuration version control
- provide software version control
- Assurance
- Ensure standardized configuration
- Provide repons on and correct any exceptions
- provide Correlation between events on different devices
- Automatically take corrective action on events and error codes
- Method to Use
- Network Management
- Python Scripts
- NETCONF
- RESTCONF
- Ansible
- Puppet
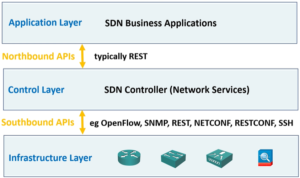
- SDN
- Cisco DNA Center
- not all methods are supported by all devices
- Choose the method(s) which is most suitable for your environment and skills
- Python, Git, GitHub and CI-CD
- Python of Network programmability
- Relatively easy to learn with many training resources
- Human readable
- Open source
- Can be installed on all popular operating systems
- Easy to find network automation code samples
- Git
- Version cotrol system for tracking changes in source code and files
- Used mainly for software dev, but can provide version control for any type of files
- Git is a distributed version control system
- Every Git directory on each computer has a full copy of the repository with history and full version-tracking abilities
- This allows multiple developers to use at the same time
- Typically there is a designated repository/master copy
- GitHub
- A Git repository hosting service
- Can be public and private
- Can be copied between users
- Management tools are avaiable
- Provide security and resolve conflicts
- CI/CD
- CI – Continuous Integration
- CD – Continuous Delivery or Continuous Deployment
- CI/CD is a set of operating principles and practices that enable appliation dev teams to deliver code changes more frequently and reliably
- Frequent changes are more efficient than rolling them up into large change windows
- Automation of building, testing and deployment allows this
- The implementation is known as the CI/CD pipeline
- Tools such as Jenkins and Travis CI aid management of the pipline
- Data Serialization Formats: SML, JSON and YAML
- Data serialization is the process of converting structureed data to a standardized format that allws sharing or storage of the data in a aform that allows recovery of it original structure
- Allows transfer of data between different systems, applications and programming languages
- Data formats are mostly interchangeable
- JSON – JavaScript Object notation
- Easier for humans to read and work with than XML
- Can be imported directly into JavaScript
- RESTful APIs often use JSON
- JSON Data Types
- Object
- Unordered collection of key/value pairs
- Surrounded by curly braces {}
- Strings and values must be a valid JSON data types
- Keys and values are separated by a colon
- Eabh key/value pair is separated by a comma
- Array
- An ordered list of values
- Surrounded by square brackets []
- Values must be a valid JSON data types
- String
- Number
- a number
- No quotes (putting it in qutoes will change it to a string)
- Boolean
- Null
- represents a blank entry
- Can be type out or field can be left blank (as long as application support blank)
- XML – eXtensible Markup Language
- Designed to describe and transfer data
- <key>value</key> contained within object tags
- YAML – RAML aint Markup Language
- Often used in Python, Perl and Ansible
- Easily read by humans
- White space (indentation) is important
- Common indentation level is considered related at the same level
- Starts with —
- Key: value representation
- – indicates a list
- Ansible playbooks use YAML